There are four types of files in Unix. They are:-
- Regular or Ordinary Files
- Directory Files
- Device Files
- FIFO Files
Regular Files:
These files usually consist of a sequential series of bytes and occupy space on the disk. They
always form a leaf node in the tree hierarchy. They have no fixed format. Their format and structure is totally dictated by the utility that creates and accesses such files.These files can be created using editors like ed,ex, vi or from the standard input using
'cat>filename' command.
An ordinary file can be a text file from a word processing package, a program written in any language of the shell etc.
Directory Files:
A directory is just a tabular collection of files and subdirectories. The contents of a directory can be any number of ordinary files, device files and directory files. A directory file can be thought of as
the branch of the Unix file system tree.Each directory has a name of normally upto 14 characters. Two or more files can have the same name if they are in different directories.
It is only the kernel which can write a directory file. It is the kernel , which updates the corresponding directory file whenever a user adds or deletes a file from it.
A user can only create directories, add or delete files from a directory ,or delete the directory itself.All the directories created by the user reside in the
home directory of the user. The
home directoryis assigned to the user when they are assigned a recognised login name. The user has complete control over the home directory; no one else except a privileged user can read or write files in it without the user's permission.
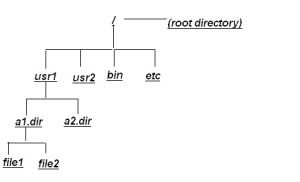
The Unix system also maintains several directories for its own use.The structure of these directories is much the same on all Unix systems. These directories which include several important system directories, are located directly under the root directory.The root directory (designated by
/) is the source of the Unix file structure; all directories and files are arranged hierarchically under it.
Device Files:
All device files(i.e terminals , printers and other hardware) in Unix are called special files. This is the key to providing
device independence. The system reads and writes to special files in the same way it does to ordinary files.However, the system read and write requests to do not activate the normal file access mechanisms; instead they activate the
device handler assosciated with the file.
The
advantage of having devices as files is that you don't need any special commands or function to access devices. The output directed to such a file will be automatically redirected to the respective physical device associated with the filename. The kernel implements this by mapping special filenames to their respective devices.For example: the user could direct the output of a process or a file-listing to the printer by using the printer name in a command.Similarly , if the user wants to print a file, the system would simply write the file to the printer device file just as it would write to any other file. This allows you to control access to any device very effectively.
All the Unix device files are stored in a directory called
/dev, which resides immediately below the root directory. Devices in the Unix file system can also be thought of as leaves in the Unix file system tree.
The special files associated with devices are not really files but pointers that point to the device drivers located in the kernel that handles data flow.Since the devices to be handled are addressed as files, the protection that is applicable to files is also applicable to devices.
There are two types of device files -
block special files and
character special files.
Block special files are for disk and tape devices.Block devices are divided into blocks (which are units of storage on the hard disk) . These blocks are used to store
i-node entries of the files.
i-nodes dictate the position of blocks through a process called
indirect addressing.
Character special files are for terminals ,printers , RAM etc. A character device is simply a device from which characters are read. They do not require the data to be buffered before it is read .
/dev/kmem and
/dev/mem are character special files for main memory.
FIFO(First In First Out) Files:
FIFO files let unrelated file communicate with each other. These files are typically used in applications where the communication path is one-way only and where a number of processes have to communicate with a single process, often called the
daemon process . Each process writes a message to the FIFO file , and the Unix system guarantees that another user will not overwrite each individual message written on the file.
Even though Unix treats all files similarly, files are categorized into the above three types because the files attributes associated with each file is different for each category.
File attributes are common to all files with slightly different interpretations.In the next post we shall discuss these file attributes.